Risk Management
Risk Management Structure
Risk Management Efforts
Our company appropriately evaluates / recognizes risks associated with our company's work execution, and defines "Risk Management Rules" for measures to prevent individual risks and measures to minimize losses arising from risks should they be actualized.
For effectiveness and efficiency in promoting Risk Management, we hold a "Risk Management Committee", and, as well as discussing our company's and group companies' internal Risk Management, we monitor critical risk matters.
Structure / Operation
Risk Management activities are summarized by the Management Planning Department, and the Management Planning Department will define the main department in charge of each risk item, and give direction on implementation of Risk Management activities.
The main department in charge will prepare a Risk Management plan and method, and, as well as taking appropriate actions, will regularly or as required report the Risk Management status to the Risk Management Committee.
At the Risk Management Committee, the reports from each main department in charge of the risk will be evaluated, to identify, review, etc., the risks requiring actions, and will discuss and study about Risk Management activity overall issues.
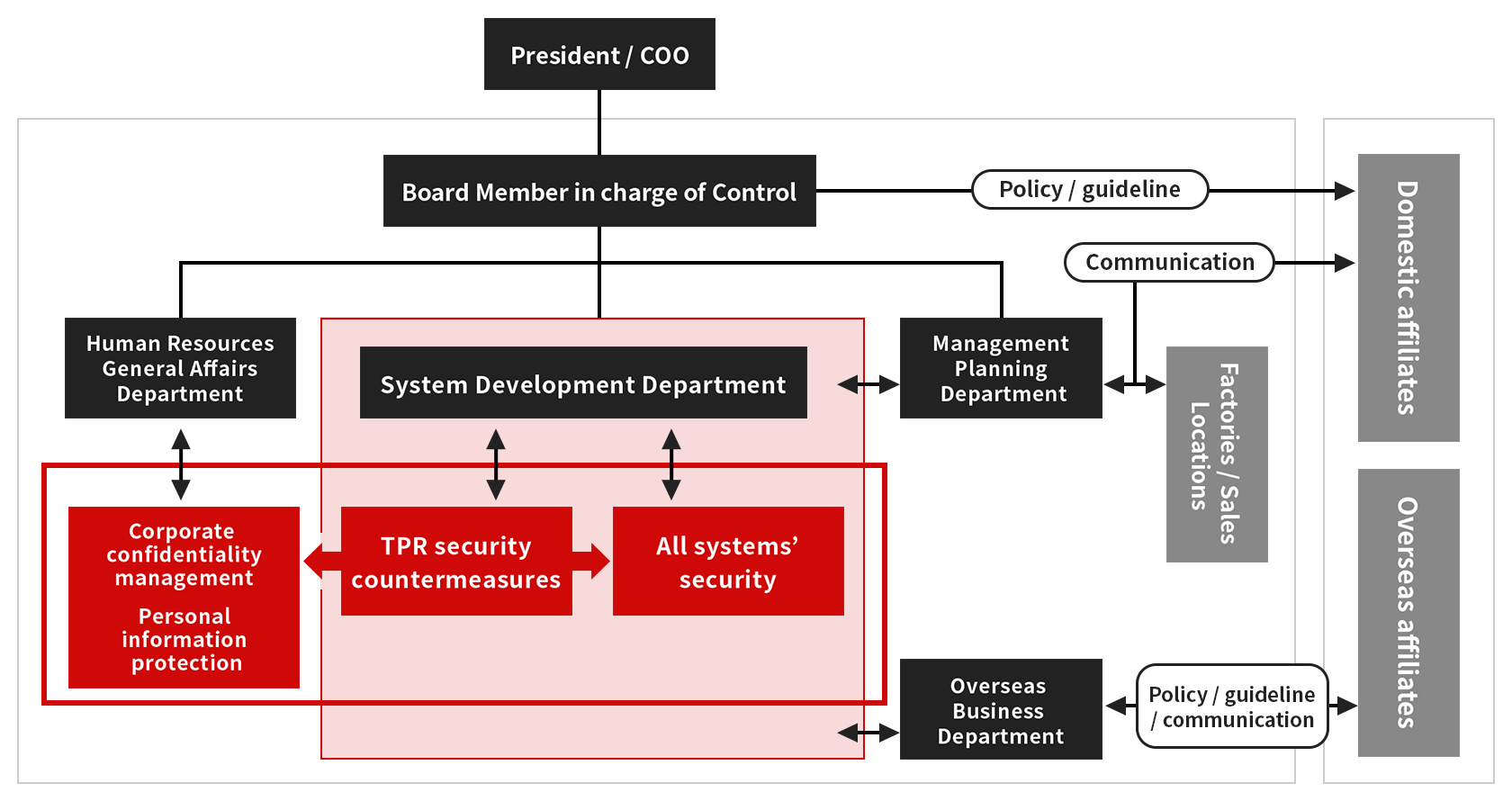
Information Security Control
TPR believes that protecting information assets is a Social responsibility. We have drafted the "Information Security Basic Policy" and work to improve our information security.
Information Security Basic Policy
- Establishment/implementation of internal rules
Based on this Basic Policy, information security rules and other rules will be put in place to implement information security measures. - Information security management structure
As well as putting in place a management structure relating to information security, a structure to communicate with external institutions etc. will be established and operated as needed. - Appropriate handling of information assets
Information assets will be appropriately gathered, managed and leveraged. Also, it is prohibited to take information assets outside the company. If information assets must be taken out, great care should be taken, and electronic documents should be encrypted. - Compliance with code and non-disclosure agreements
Compliance with information security related code such as the Personal Information Protection Law and non-disclosure agreements with customers will be enforced. - Information security education
To enforce this policy, Board Members and employees (including contract employees, agency employees, etc.), group company employees and partner company employees will regularly and on an ad hoc basis be given information security education.
- E-learning
- Targeted email training
- Responding to an information security accident
In the unlikely event of an information security accident, speedy actions and recurrence prevention measures will be implemented. Also, if the accident needs to be reported to a customer or oversight institution, the report will be given quickly. - Information security audit
To enforce information security, regular internal audits of information security countermeasures will be implemented. Internal audit documents are submitted to the auditor for external audit. - Continuous improvement of information security countermeasures.
Information security countermeasures are reviewed and continuously improved in response to legal schemes, Social trends, audit results and autonomy, etc. - Information security management structure
Business Continuity Management (BCP)
"A business continuity plan (BCP) defines the goal and basic policy in case of an emergency situation such as a large-scale disaster, etc. With the background of the increasing importance of BCP in recent years, to make the content more practical, a BCP Meeting is held across locations once every month, with activities including creation and review of various disaster response manuals.
Also, we maintain a business continuity structure for both hard and soft aspects, such as a personal safety confirmation system, maintenance of an emergency contact network, securing of emergency communications methods, stockpiling of goods needed for recovery, and regular education/training."
